Introduction
Cybersecurity has become more important in recent years as the threat landscape has changed in the past few years. There are several reasons for this including the proliferation of state and non-state entities, individual cybercriminals and others who have the capability and resources for these. On the other hand, businesses have to play a catch-up game to thwart these attackers. Previously, the worry over these incidents were on financial losses, business disruptions and cascading effects on the industrial supply chain due to forced shutdowns, but now these can also be potential ways to deliberately cause industrial accidents such as fires, explosions and loss of containment in case of industrial targets.
In this article, we will understand how we can increase the cyber resilience of process industrial plants, if we take appropriate actions, starting at the design stage itself and then at every stage of the project. This helps create systems that can be used to ensure cybersecurity at all stages of the plant lifecycle, after the project is completed and even later on after the plant starts production.
Past cyber incidents
Cyber-attacks on process industries are relatively new phenomenon that accelerated in the past decade. Not all incidents are announced to the general public. Some of the notable ones that received wide publicity, are listed below, with brief descriptions of each incident. These examples have been given to give an idea of the different kinds of incidents that can possibly occur.
1. Colonial Pipeline incident [1]
In May 2021, Colonial Pipeline company, which is one of the largest petroleum pipeline operating companies in North America, suffered a cyber-attack, that forced them to shut down a large part of their pipeline operations, leading to supply shortages all along the US East Coast.
2. Stuxnet- Natanz Uranium enrichment facility [2]
The Stuxnet malware found its way into the control and automation systems of Iran’s Natanz Uranium enrichment facility, where it could manage to physically damage centrifuges used to process uranium. It is not clear if in addition to largescale damage of equipment, if any personnel injuries occurred.
3. TRITON- Saudi Arabian petrochemicals plant [3]
The Safety Instrumented System of this plant was attacked with malware and it could have caused a disaster, however alert control room staff noticed it happening and they could manage to safely shutdown the plant. In this case it was a near miss, if it had succeeded, it would have resulted in a large industrial disaster.
Are these the only ones? No, there are many more of such incidents, but such news is not widely reported for fear of giving ideas to potential perpetrators, as well as to prevent panic in the public.
According to an Industrial cybersecurity expert, writing for Control magazine, in reality there are more than thousands of incidents each year [4], that go unreported or misreported. Many of the incidents are either deliberately, or mistakenly, not attributed to cyber-attacks, but to mysterious failures of equipment. The investigation findings rarely make their way into the public discourse, unless it directly affects the public, such as the colonial pipeline incident.
Note that these are only attacks against companies in the process industry sector; other industry and business sectors, which are also subject to such attacks, are not the subject of this article.
The point of mentioning this is that the cyber threat to industrial plants is real, not theoretical and we should take steps to protect our plants from cyber-attacks. These cyber-attacks can happen anytime during a plant’s lifecycle and if addressed at the project stage itself, can help reduce lifetime enterprise risk.
This article gives a broad overview of how this can be implemented.
We will start from the basics.
Two Types of Systems
There are mainly two types of computer-based systems in the process industry, which we refer to as IT (Information Technology) systems and OT (Operational Technology) systems.
IT systems mainly process information, without controlling any physical objects or parameters. Examples of IT systems are ERP systems, other Management Information Systems (MIS), Logistics & Dispatch Management systems, smart Process Design systems that use CAD, Process simulation systems, Maintenance Management systems, Incident reporting systems and so on. All of these basically process information, but do not directly control any physical equipment.
OT systems are cyber-physical systems, which means they are computer-based systems that control physical equipment.
Examples of OT systems are industrial control, automation and safety systems (called as IACS for short), Electrical substation control systems, pipeline SCADA systems, (SCADA stands for Supervisory Control and Data Acquisition systems), Building Management Systems (used for HVAC, access control, etc) and Fire Alarm Systems.
For example, an IACS will open/shut valves, start/stop pumps and other equipment. A Building Management System (BMS for short) may control door opening, move air dampers, start/stop blowers and other equipment. Fire alarm systems can be for fire detection as well as firefighting, where they may operate fire water pumps and other equipmnt.
Two types of cyber incidents
There are mainly two types of cyber incidents.
One is an attack which happens directly on IT systems, that consequentially affect the plant’s OT systems. This means that the OT system is not under attack, but because the attacked IT system can no longer communicate with the OT system, that is also affected. This happened in case of the Colonial Pipeline incident, where the IT systems were attacked and due to the business processes that were in use, the OT systems became unusable and had to be shut down. Since the OT system shut down the pipeline also had to be shut down.
The other type of incidents, are where the OT systems are directly attacked. In the Stuxnet attack for example, the OT systems were directly attacked that physically damaged the uranium centrifuges. That IACS was completely isolated from the internet and other external systems. Whether any harm occurred to personnel or any environmental damage occurred is not known, as there was an information clampdown from the authorities.
Process industries must guard against both types of attacks, as the business needs both IT and OT systems to function normally, in order to run the business.
OT cybersecurity and IT cybersecurity
OT cybersecurity and IT cybersecurity are different and need different tools, different types of skills and different approaches. Using IT cybersecurity tools and practices, is either not possible at all in the OT domain, or it may actually do more harm than good if used. OT cybersecurity is often referred to as Industrial Cybersecurity, which makes it clear that we are talking about cybersecurity of Industrial Systems.
Hence process industries need both skillsets, plus some people who have knowledge about both domains.
Cybersecurity of the plant is not a pure IT issue
Process Industry Asset owners and operators should understand that cybersecurity of the plant is not a purely IT problem. It is an OT problem and requires the plant’s operations and maintenance team, as well as the safety team, to have specialized knowledge and skills for ensuring Industrial Cybersecurity. Additionally, all plant personnel are collectively responsible for a good cybersecurity posture of the plant, just like all plant personnel are responsible for safety of the plant.
Many older process plants have IACS that were designed and procured before cybersecurity was an issue and hence are vulnerable to cyber-attacks. We can of course try to modify these systems and institute new processes to improve their security posture, but there are challenges in doing so.
Why consider cybersecurity at the design stage?
Bolting on security after the plant is built, is difficult to do and is not a good idea, besides being more expensive to implement and maintain. This is done only for older plants because we have no choice. We cannot rip off everything and start anew for older plants.
For a brand new plant, however, we can implement cybersecurity design concepts from day one, so that we can build a plant that will be cyber resilient always.
The project itself should be executed with cyber resilience to reduce the risk of delays and disruptions, or loss of intellectual property, due to a cyber incident.
Project Phases & the plant’s lifecycle
A typical process plant starts out as an idea. Once the conceptual idea is ready with some baseline figures, such as “Let us build a greenfield 100,000 tonnes per annum 1-Diethyl-xyz manufacturing facility in ABC Industrial area, near the port of XYZ, in country GHI. The project should take 18 months from start to commissioning and the plant is expected to run for at least 30 years, as we see a strong and growing demand for this product and several supply shortages as some older plants get decommissioned and nobody else is building a new plant to make this”.
After this project is approved by the company management, the various stages are as given in Figure 1. During each stage of the project and thereafter (once commissioned), cybersecurity has to be ensured.
IT security and OT security during the project
Note that from Figure 1, you will realize that even though a typical plant like this, uses a lot of OT systems (such as for example IACS, Fire & Gas Systems, Building Management systems), during the project, we have to consider both IT security as well as OT security.
For example, the systems via which the engineering design is carried out, are all IT systems, where hundreds of engineers will work on design and drawings of the project. It is important to have cybersecurity to not only protect Intellectual Property (prevent stealing of designs and data), but also to avoid disruptions due to cyber attack, that can destroy the design data or delay the project timelines.
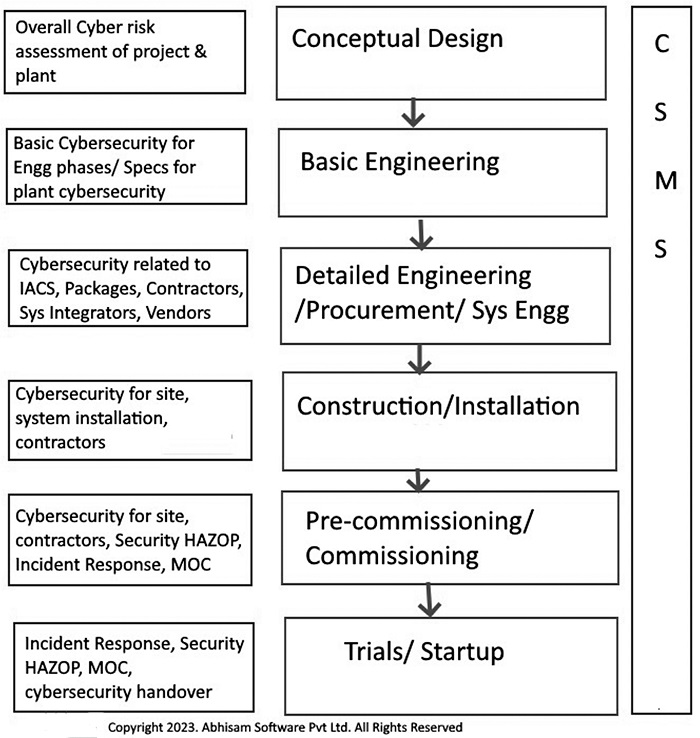 Every phase of the project has cybersecurity requirements, which will get progressively more complex as multiple vendors, contractors, consultants, and others start their work, exchange data and drawings, remotely access various data, hold online meetings and so on, which all need robust Information security and IT cybersecurity.
Every phase of the project has cybersecurity requirements, which will get progressively more complex as multiple vendors, contractors, consultants, and others start their work, exchange data and drawings, remotely access various data, hold online meetings and so on, which all need robust Information security and IT cybersecurity.The OT security requirement specifications must start as early as possible, even during the concept phase itself, when you will be carrying out various concept HAZOP studies and similar safety and environmental impact studies. Cyber vulnerabilities and their effects on the plant’s safety must start in this phase itself.
In the basic engineering phase, the IACS and other OT system specs must include cybersecurity requirements. Safety studies done during this phase must account for cyber incidents.
This indeed is a lot of work, but it can be managed well with a robust Cybersecurity Management System in place, which will involve all stakeholders including the IT side as well as the OT side. All members of the project team should be made aware of it and the importance of managing it well.
After the trials end and the startup is successful, the project team will hand over to the plant’s operations team.
Parallels with the Safety Lifecycle
Many of us are familiar with the concept of the Safety Lifecycle, but we will take a look at it again, to have an insight on the similarities with cybersecurity.
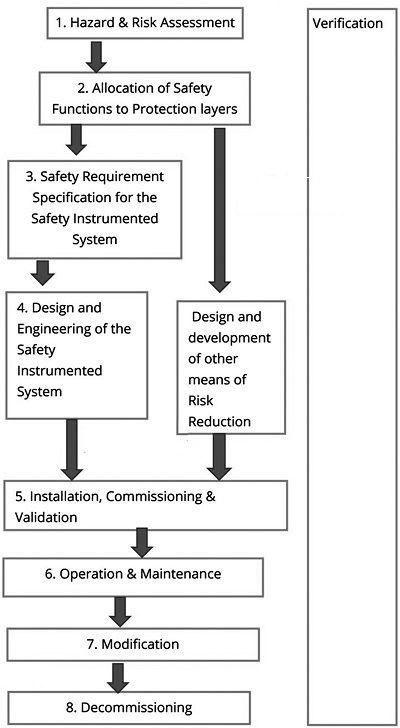
The basic idea of the Safety Lifecycle, is that safety is not a one-time activity or stage of the project, but a continuous process. We need to ensure safety throughout the lifecycle of the plant starting from the concept stage (where we may carry studies like Concept HAZOP), right up to the time that the plant is decommissioned (where we carry out a Decommissioning HAZOP). In between these two phases, we have to continuously ensure that the plant continues to operate safely. This Safety Lifecycle for a process industry plant is shown in Figure 2. It is based on the one given in the international standard IEC 61511-Functional Safety -Safety Instrumented Systems for the Process Industry sector[5].
Poor cybersecurity can adversely affect safety
Why should we bother about cybersecurity of the plant? Why should we follow a lifecycle approach?
 Poor cybersecurity at the plant level, can not only result in disruption of operations, but also result in theft of intellectual property (such as production recipes and processes, other process & equipment know how), or can cause accidents such as fires, explosions, toxic releases and similar incidents. Since cyber-attacks are notoriously hard to attribute, there are very few ways to find the real perpetrator. Therefore, it has become a preferred method of not only cyber criminals (who hope to earn ransom by disabling systems and demanding payment in order to restore them), but also state and non-state actors, who may act due to different motivations, such as a grouse against the company’s policies, or as means of attacking the country that hosts the plant. In these cases, they are not interested in money, they are only interested in sabotage of the plant or causing a disaster.
Poor cybersecurity at the plant level, can not only result in disruption of operations, but also result in theft of intellectual property (such as production recipes and processes, other process & equipment know how), or can cause accidents such as fires, explosions, toxic releases and similar incidents. Since cyber-attacks are notoriously hard to attribute, there are very few ways to find the real perpetrator. Therefore, it has become a preferred method of not only cyber criminals (who hope to earn ransom by disabling systems and demanding payment in order to restore them), but also state and non-state actors, who may act due to different motivations, such as a grouse against the company’s policies, or as means of attacking the country that hosts the plant. In these cases, they are not interested in money, they are only interested in sabotage of the plant or causing a disaster.Cybersecurity at each Phase of the Lifecycle
We should implement cybersecurity for every phase of the plant’s lifecycle starting from the phases in the project lifecycle to after the plant commissioning, where it will be applicable to the phases of the plant’s lifecycle, until it is decommissioned.
This implies a structured and well-planned approach to cybersecurity, which means we require a management system to implement it. If you think about it, conceptually a Cybersecurity Management System has similarities with a Quality Management System, or a Safety Management System. Note that a CSMS does exist in many companies, but it is only for the IT related systems. We should have a CSMS for OT systems too and it should be applicable right from the conceptual phase of the project.
Cybersecurity Management System for the plant
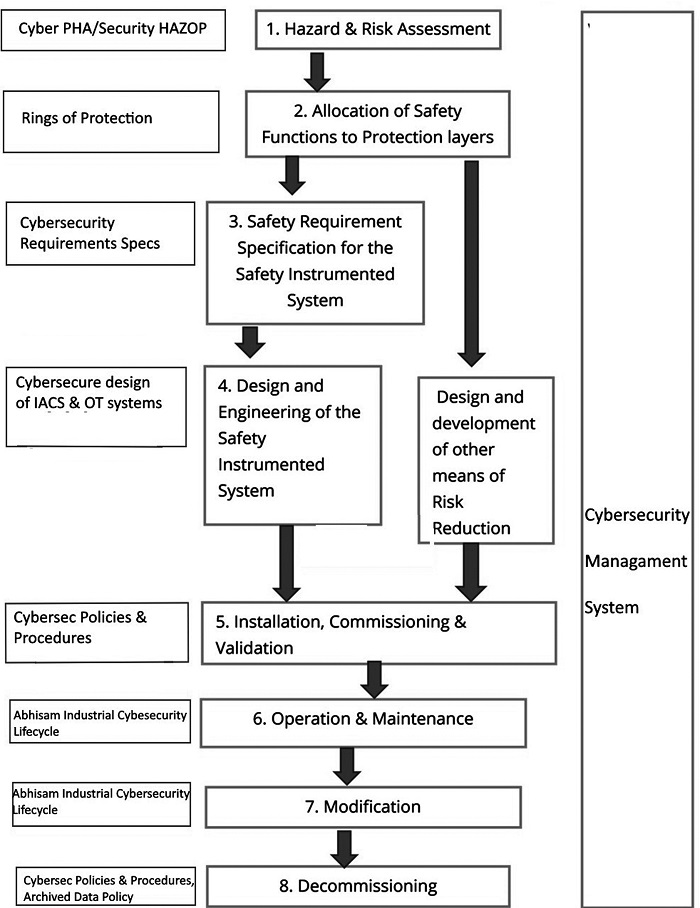
Such a CSMS can either be integrated into the company CSMS, or it could be a separate CSMS at the level of the plant management. It is up to the company management to think and decide which approach works best. However, remember that the personnel who are responsible for the plant level CSMS should be well versed in securing OT systems, as IT security and OT security are different domains.
Although the figure 2, is meant for the development of a Safety Instrumented System for a process plant, it is useful to understand for implementing cybersecurity for a process plant too, during the entire lifecycle of the plant.
Such a lifecycle is shown (Figure 3).
A brief explanation of the cybersecurity requirements for these phases is given here.
1. Cyber PHA/Security HAZOP
This is done along with the normal Hazard and Risk Assessment studies that use methods like HAZOP, What-If, LOPA and similar, to ensure that the Hazard and Risk assessment study includes the consequences for cyberattacks. This is because cyberattacks can disable the plant’s Control and Safety systems and countermeasures need to be developed to ensure that safety does not get compromised, even if the IACS is disabled. A Security HAZOP can help us find these scenarios and ways to add additional protective measures.
2. Rings of Protection / Allocating layers
This is similar to the LOPA Study carried out for safety functions, to ensure that there are enough cyber protection layers, in other words, “Rings of Protection”.
3. Cybersecure Design of IACS and other OT systems / Safety Requirements Specifications
This phase has to ensure that specs for IACS & other OT systems include cybersecurity specifications, and the design and architecture of the system is cybersecure.
4. Cybersecurity Policies and Procedures during Installation and Commissioning
Although there would a Master document containing cybersecurity policies and procedures for the company and the project, which could be part of the CSMS, there is a need for special cybersecurity policies and procedures that are applicable only during the installation, pre-commissioning and commissioning phases, when several contractors, outside parties, various vendors and system integrators for the IACS and other OT systems are all present at site. In this phase, both IT security as well as OT security considerations apply.
5 & 6. Industrial Cybersecurity Lifecycle – Plant Operations phase and Modifications phase
Once the plant is commissioned and starts production, the Industrial Cybersecurity Lifecycle*[6] can be followed. This is shown in Figure 4.
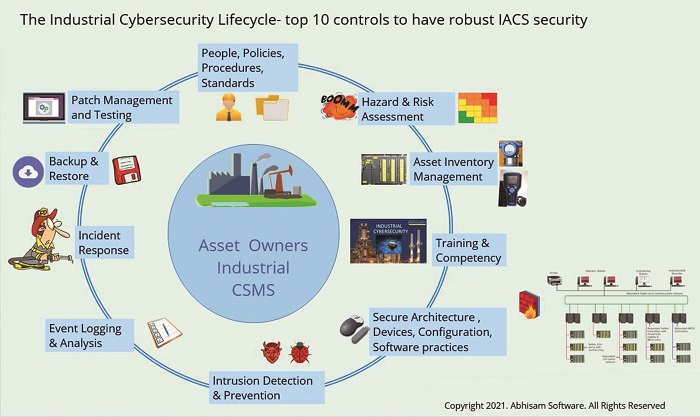 The operations phase is one of the longest phases of the lifecycle and can run for several years (in our example with the new plant, this period is 30 years), so it is very important that during this period, cybersecurity does not degrade over time, even after modifications to the plant that may take place during this long period.
The operations phase is one of the longest phases of the lifecycle and can run for several years (in our example with the new plant, this period is 30 years), so it is very important that during this period, cybersecurity does not degrade over time, even after modifications to the plant that may take place during this long period.There are several versions of OT Cybersecurity lifecycles. However, most of them do not take the unique features of the process industry into account. Hence Abhisam has developed the below Industrial Cybersecurity Lifecycle which is relevant to the process industry sector.
Here is a picture that shows the Industrial Cybersecurity Lifecycle* (Figure 4)
7. Decommissioning Phase
During this phase, special cybersecurity policies and procedures must be developed to ensure that intellectual property such as plant process data, recipes, historian data and other kinds of data is either properly archived or destroyed/prevented from unauthorized access.
Safety culture and cybersecurity culture
As an asset owner, implementing cybersecurity in the project and then later at the plant level is a challenging job. It requires a change in the company culture. This has parallels with Industrial Safety, where it has been found that having a good safety culture in the organization always improves the overall safety of the plant and leads to a drastic reduction in the number of safety incidents.
Similarly, a good cybersecurity culture must be developed during the project lifecycle and maintained later on, after the plant is commissioned. Even the best CSMS, or IT security or OT security systems cannot work without the people who use it being fully committed to it. Many security breaches happen due to human ignorance and errors and thus if a robust cybersecurity-aware culture is nurtured, your plant will have far less risk of being a victim of a cyber attack.
Standards and Practices
There are several cybersecurity standards for both IT security and OT security, such as IEC 62443 (not all parts have been published so far, but the published parts can be useful), ISO 27001, NIST 800-82 and others.
You need to study which of them are applicable to your plant or facility. In some cases, this may depend on the industry sector, or the jurisdiction where the plant is located. Although cybersecurity standards are important to understand and apply, these are the baseline. They are good to use and apply, but implementing them does not automatically ensure complete cybersecurity, as each project and plant in the process industry sector is unique in its own way. There is no one fits all magic standard or solution available. Hence a boilerplate product or solution may not work.
You also need to find out if any cybersecurity directives or regulations apply, as these are mandatory by law and have to be complied with. Even within the process industry they differ for different sectors, as well as in which jurisdiction the plant is located.
Competencies Required
You not only need competent people to be in charge of your IT security and OT security, you also need all your project and operations personnel to have working knowledge of both IT and OT cybersecurity, with a robust Learning Management System with appropriate learning courses, with assessments, which helps you upskill them and maintain their competency at all times.
This is often overlooked and a reason for many cyber incidents happening.
Role of Insurance in mitigating cyber risks
There is often a myth prevailing among some decision makers, that it is not necessary to do all these things, it is enough to have a rudimentary CSMS, enter some legal clauses in contracts with vendors and contractors regarding cybersecurity and then take out an insurance policy.
Although cyber insurance is a good idea, it is not a substitute for a good cybersecurity posture. In the past, there have been famous cases, where the claims were challenged and ended up in courts[7]. The difficulty in attributing responsibilities for cyber attacks means that if a state actor is suspected to be behind the attack, it can be deemed to be an “act of war”, which is generally not covered in many policies. Hence, it would be prudent to consider experts in this field before taking out such policies and in any case an insurance policy should be an additional risk reduction measure, not the primary one.
Roadmap to implement cybersecurity for your project
This article here can be used as a starting point to build a roadmap to implement a robust cybersecurity plan for your next grassroots project.
Conclusion
Cybersecurity is a growing concern in the process industry. Past incidents demonstrate that cyber-attacks can not only disrupt operations but can also be the cause of industrial accidents that can damage assets, injure people and damage the environment. We need to build in cybersecurity at the plant’s initial concept design stage itself, followed by further cybersecurity related actions during each stage of the project and later on also during the plant’s operational phases too. This will greatly reduce the risk of a cyberattack affecting the plant and consequential damages, leading to a lesser level of overall risk to the enterprise.
References
- Colonial Pipeline Cyber Incident https://www.energy.gov/ceser/colonial-pipeline-cyber-incident
- Countdown to Zero Day- Stuxnet https://icdt.osu.edu/countdown-zero-day-stuxnet-and-launch-worlds-first-digital-weapon
- Attackers Deploy New ICS Attack Framework “TRITON” and Cause Operational Disruption https://www.mandiant.com/resources/blog/attackers-deploy-new-ics-attack-framework-triton
- More than 17 million control system cyber incidents are hidden in plain sight- Joe Weiss, Controlmagazine https://www.controlglobal.com/blogs/unfettered/blog/21438102/more-than-17-million-control-system-cyber-incidents-are-hidden-in-plain-sight
- IEC 61511-1:2016 -Functional safety – Safety instrumented systems for the process industry sector https://webstore.iec.ch/publication/24241
- The Abhisam Industrial Cybesecurity Lifecycle- Top 10 controls to protect your IACS https://www.abhisam.com/industrial-cyber-security-lifecycle-top-10-controls-to-secure-your-iacs/
- Mondelēz settlement in NotPetya case renews concerns about cyber insurance coverage https://www.cybersecuritydive.com/news/mondelez-zurich-notpetya-cyber-insurance-settlement/636029/
- The figures in this article are conceived and made by Abhisam who own the copyright for the same.
- The views expressed in the article are the author’s own and may not reflect the views of Abhisam.































