Abstract
With widespread digitalisation of industry and business, plant wide internet interconnectedness across geographies, external cloud and so on, cybersecurity has become crucially important, and all the more so, in a highly knowledge and know-how based chemical industry. Cyber attacks could come from anywhere: from competitor rivals to countries wanting to steal know how or damage to even from terrorists.
This article is therefore very timely and covers in detail the various challenges involved in cybersecurity management. The article is based on key insights shared by cybersecurity experts from a range of industrial companies.
Introduction
Today, most industrial companies have two separate cybersecurity programs. Cybersecurity professionals in the CIO’s organization ensure the security of corporate data, IT assets, networks, and business applications. Technical personnel in operations and engineering take care of the security of OT networks and assets.
Differences in IT and OT technologies, goals, and environments justified the development of separate security programs. However, today’s siloed programs are leaving many plants especially in the chemical and oil and gas industries at risk of a serious cyber incident. OT cybersecurity programs often lack the resources, expertise, and supporting technology to maintain defenses, manage attacks, and secure the new technologies being deployed in operating facilities. CISO efforts to manage security are also being hampered by the lack of OT system visibility and access.
The situation is likely to get worse unless companies act. The industrial cyber threat environment is already becoming more challenging with ransomware, sophisticated attacks like Solar Winds, and the explosion of digital transformation programs. These developments demand proper maintained, end-to-end security of all corporate activities and rapid detection and response to all anomalous events. While most industrial IT security programs have the cyber professionals and advanced security solutions to deal with these new challenges, many OT security programs are still struggling to achieve yesterday’s requirements.
IT/OT cybersecurity convergence offers a cost-effective way to address current and future OT security challenges. IT cyber professionals can fill critical resource and expertise gaps in OT security programs. Common cybersecurity processes can eliminate security gaps between IT and OT systems. Use of similar technologies can enhance visibility and incident response effectiveness.
While convergence offers many benefits, experience shows that combining IT and OT programs can be challenging. Successful convergence efforts have clear convergence goals and proven approaches for addressing critical issues like cultural differences and OT reluctance to use conventional IT security practices and technologies. This article presents some of the lessons learned by leading companies that are already on cybersecurity convergence journeys, with a special slant on the chemical and oil and gas sectors.
The Different Goals of IT and OT Teams
Industrial cybersecurity teams face an awesome set of responsibilities and challenges. IT security teams, which are often part of the CIO’s organization, are responsible for managing the security of a wide range of information processing technologies, including workstations, servers, networks, printers, websites, cloud applications, and mobile devices. This includes ensuring the confidentiality of all corporate information and the continuous availability of critical business systems and applications.
OT security teams are commonly assigned to specific facilities and commonly report to plant managers or corporate engineering managers. These people are responsible for ensuring the availability and integrity of control systems, SCADA systems, and a diverse collection of cyber physical systems like robots, packaging systems, etc. Managers expect them to prevent any cyber incidents that might impact safety, product quality, environmental compliance, or operational continuity.
While IT and OT security teams may collaborate on security of interfaces, decisions about OT security within facilities are generally made and funded locally, based on each site’s risk appetite, capabilities, and preferences. IT cybersecurity programs are generally more advanced than those in OT.
The picture is quite different for industrial OT cybersecurity programs. While many sites recognize the need for OT cybersecurity, they rarely invest in more than the basic passive defensive technologies recommended by industry groups. Many also neglect the need to invest in people and solutions to maintain these defenses.
Converging Security Processes
Ransomware and sophisticated attacks have clearly raised top management concern about cyber-attacks. They expect that IT/OT cybersecurity convergence efforts will provide them the visibility and confidence they need to be sure that all cyber risks are being properly managed across all systems and assets. Consistent security metrics, policies, and processes are essential for this goal.
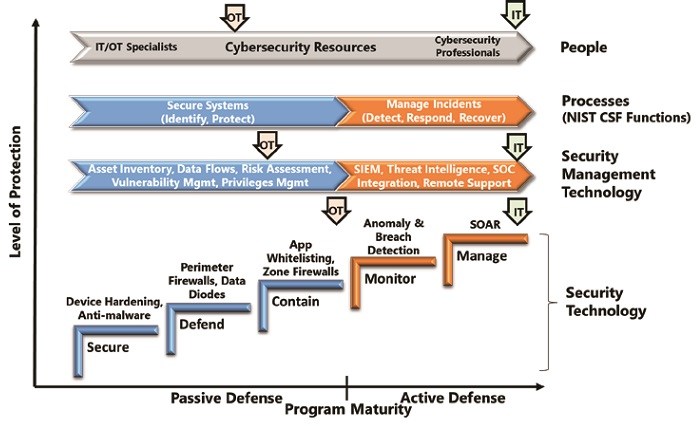
A common cybersecurity framework provides the foundation for driving consistency across IT and OT cybersecurity efforts. It enables people with significantly different backgrounds to agree on key security issues and the actions needed to address them. An effective framework is comprehensive yet abstract enough to avoid specific implementation details and conflicts about specific security practices and technologies.
Many companies have adopted the NIST Cybersecurity Framework as the overall framework for IT/OT cybersecurity convergence. The completeness of this framework and its general acceptance ensure that all issues are addressed. This framework also provides guidance to specific IT and OT practices, in standards like IEC-62443, NIST 800-XX, and ISO 27000, that can help companies meet the requirements. Some companies have also used the CIS 20 to guide discussions. OT security teams will likely have concerns about the use of IT technologies and practices in OT. But these can be alleviated by ensuring that they are involved in these decisions and can ensure that critical OT constraints are properly considered and respected.
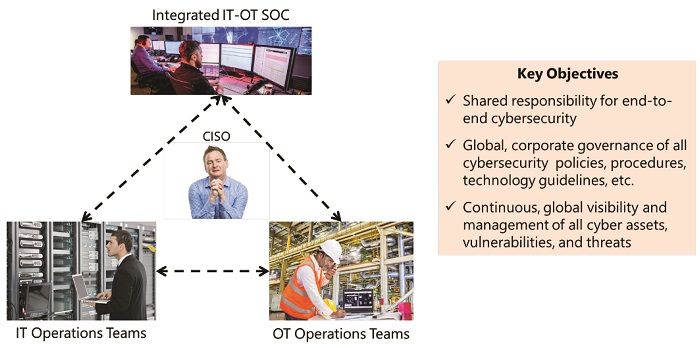
Regardless of the formal reporting structure, converged IT/OT cybersecurity programs generally have a single person who is responsible for cybersecurity. Most often this is the CISO, or the CIO when the CISO is part of the IT organization. This person establishes security policies, monitors compliance, and prepares periodic cybersecurity reports for top management. They may also be charged with setting specific security objectives, managing third-party security agreements, and developing recommendations for new cybersecurity people, processes, and technologies.
Setting an Appropriate Convergence Goal
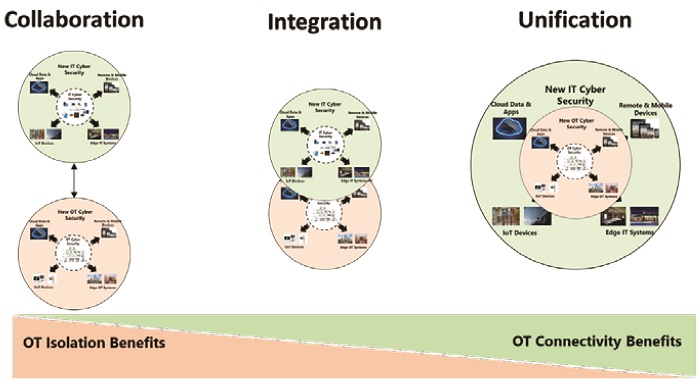
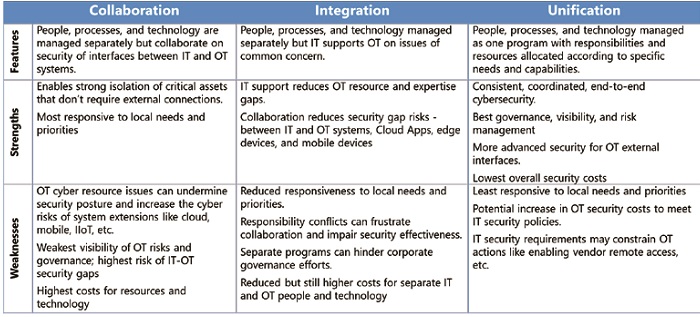
Many industrial organizations have launched IT/OT cybersecurity convergence programs, but the goals vary significantly. Some want to maintain separate IT and OT cybersecurity programs but improve collaboration in securing system interfaces. Others want to integrate efforts in key areas, like DMZs, where OT uses conventional IT technologies and can support common IT security products and practices. Still others are targeting a complete reorganization of people, processes, and technologies to create a unified corporate cybersecurity program.
These differences reflect the tremendous variations that exist in industrial facilities and digital transformation goals. Some companies have critical operations where a cyber incident could have devastating impacts. Others have simple operations that can tolerate minor OT system disruptions. Some facilities can reap tremendous value from new technologies and OT connectivity, while others see little or no benefits. And many industrial cybersecurity teams need to deal with facilities in all of these categories.
Recognizing the benefits of different convergence goals is essential for establishing rational site-specific programs. Building a converged IT/OT cybersecurity program will ultimately involve some changes to security people, processes, and technologies. The willingness of operational managers to support these changes depends upon the costs and benefits that will be generated.
Regardless of a program’s goals, there are certain guidelines that should be considered in every IT/OT cybersecurity convergence program:
- IT and OT cybersecurity are equally important. Industrial companies need to protect information, people, and operating assets throughout the corporation to ensure business continuity.
- Convergence is more than just transferring OT security to IT security teams. Conventional IT technologies and practices may work in certain OT system areas, but others will always require people with unique expertise, familiarity, and local access.
- Convergence pace will vary across sites, so convergence plans must anticipate support for sites at different stages of their convergence
Convergence is Primarily a People Problem
ARC research consistently shows that people represent the biggest challenge for IT/OT cybersecurity convergence programs. Much of this is due to the cultural differences between people who work in office and plant environments. IT and OT security people also have different skills, perspectives on the challenges and approaches to security management.
Building trust between IT and OT personnel is essential but challenging. Successful efforts foster trust through collaborative involvement of both groups in the development of security metrics, standards, policies, and processes. This facilitates effective teamwork through common terminology, shared understanding of risks, and recognition of individual strengths. It also helps to focus everyone’s attention on the issues that represent the highest risks to the organization.
Gaining support from operations and engineering managers is equally important. This requires successful interactions that demonstrate IT respect for plant performance goals. Many companies find that plant engineers are happy to offload responsibility for cybersecurity tasks like patching, once they are confident that cybersecurity professionals won’t create problems for normal system operation.
Retaining cybersecurity resources is another issue that needs to be addressed when planning convergence programs. The general shortage of cybersecurity experts makes it hard to replace these critical people. Managers need to ensure that employees find assignments rewarding and create opportunities for advancement along well-defined career paths. Framing cybersecurity as a separate profession with cross-training opportunities can help in this regard.
Attention must also be given to the role that third parties can play in satisfying resource requirements. This can enable companies to offload some tasks and ensure that permanent employees have the necessary time to focus on critical issues like vulnerability and threat management. Many industrial companies rely upon third parties for security assessments, penetration tests, audits, workshops, and table-top exercises.
End User Perspectives on IT/OT Cybersecurity Convergence
At the ARC Industry 2021 Forum, users from the chemical and oil and gas sectors discussed the people and process challenges of IT/OT cybersecurity convergence. They highlighted the need to move away from the “them vs. us” approach. What works best is combining efforts, talking to each other, and replicating best practices. As systems evolve, it is important to have a cross-fertilization of ideas, experiences, and skillsets to arrive at a single solution – this is the winning way. The entire session can be watched here.
In a second IT/OT cybersecurity convergence session, another set of users discussed the technology challenges. Consensus was that convergence of technologies across IT and OT boundaries gives better outcomes. Securing OT systems and getting the basics right is not easy, they opined. So, instead of reinventing the wheel, proven solutions/techniques can be taken from the IT world and tweaked to suit OT needs. The session can be viewed here.
Recommendations
Many industrial companies are working to converge cybersecurity efforts across business areas and technology domains. Reasons vary but they all see convergence as a way to address a variety of OT cybersecurity challenges including lack of resources, more sophisticated attacks, and digital transformation. ARC research suggests that these benefits can be achieved if companies set appropriate convergence goals and take steps to avoid the major obstacles that can derail their efforts.
ARC has been researching IT/OT cybersecurity convergence for many years and this topic has been the focus of numerous cybersecurity workshops at ARC Forums. The information in this report summarized some of the key insights shared by cybersecurity leaders from a range of industrial companies who have been involved in these discussions. While every company has unique challenges, they will still face similar challenges as they strive to change cybersecurity status quo. Our hope is that this report will help you overcome those challenges.
Based on this and related research, ARC recommends the following actions for owner-operators and other technology users:
- Set realistic goals for your cybersecurity convergence efforts and plan to achieve that goal incrementally using the goals we described as collaboration, integration, and unification. The benefits achieved at each step will garner the support you will need to continue the journey.
- Adopt an overall cybersecurity framework to build your team, identify next steps, and focus your efforts to converge people, processes, and technologies.
- Address people, processes, and technology challenges in that order.
- Consider establishing cybersecurity as a specific discipline within your company. This can ease human resource issues if you choose to develop a single cybersecurity organization.
- Be realistic in your expectations – change takes time. Recognize that every improvement is a step to your ultimate goal of safe and secure operations.
m
All this and more will be discussed at the 26th Annual ARC Industry Forum from February 14-17, 2022 (physical event, Orlando) and March 7-10, 2022 (online).